

Endpoint security has quietly become one of the most important line items in modern IT budgets. As ransomware, fileless malware, and identity driven attacks increasingly target laptops, servers, and mobile devices, organizations are shifting away from basic antivirus toward full endpoint protection platforms that combine prevention, detection, and response.
In 2026, endpoint security is no longer a single product category. It is an ecosystem of EPP, EDR, and XDR capabilities delivered through cloud native platforms, often bundled with managed services. Pricing reflects that complexity, ranging from entry level tools for small businesses to advanced enterprise systems costing hundreds of dollars per endpoint each year.
This guide breaks down what endpoint security really includes in 2026, how pricing works, and how leading platforms differ in features, strengths, and ideal use cases.
Endpoint security has evolved far beyond traditional signature based antivirus. Modern platforms rely on machine learning, behavioral analytics, and automated response to stop threats that never touch disk or reuse known malware patterns.
Several forces are shaping the market this year:
● Remote and hybrid work has expanded the attack surface far beyond corporate networks
● Ransomware groups increasingly target endpoints as the initial access vector
● Cloud first architectures favor lightweight agents and centralized consoles
● Security teams face talent shortages, accelerating demand for automation and MDR
As a result, cloud delivered EDR and XDR platforms dominate new deployments, especially those that integrate cleanly with SIEM, identity, and zero trust frameworks.
While vendor terminology differs, modern endpoint security platforms in 2026 are built around a shared technical foundation designed to detect threats that traditional antivirus can no longer see. These features work together, not as isolated tools, but as layers of visibility, analysis, and response that operate continuously across every endpoint.
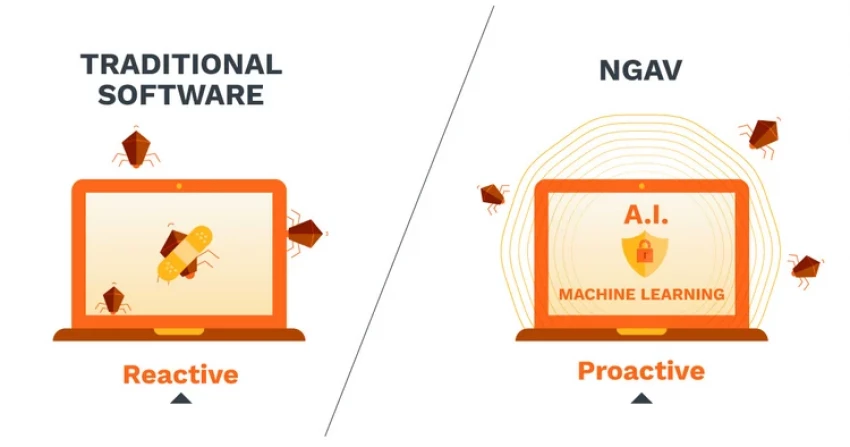
Next generation antivirus (NGAV) is the baseline layer, but it bears little resemblance to legacy signature-based scanning. Instead of matching files against known malware hashes, NGAV engines analyze behavior in real time. They monitor how processes execute, how files interact with memory, and how applications attempt to access system resources. Machine learning models trained on billions of benign and malicious events identify anomalies such as unusual process spawning, credential dumping behavior, or unauthorized encryption activity. This allows NGAV to block zero-day malware, fileless attacks, and living-off-the-land techniques that never write a malicious file to disk.
Endpoint Detection and Response (EDR) builds on this foundation by recording detailed telemetry from every protected device. This includes process trees, command-line arguments, registry changes, network connections, and user activity context. Rather than simply blocking threats, EDR creates a searchable timeline of events that allows security teams to understand how an attack unfolded. When an alert is triggered, analysts can trace lateral movement, identify patient zero, and determine whether an incident was contained or spread across the environment. In practice, EDR transforms endpoint security from prevention-only into continuous detection and investigation.
Automated response and remediation addresses the reality that human response time is often too slow for modern attacks. Ransomware can encrypt an endpoint in minutes, and credential theft can propagate even faster. Automated response capabilities allow platforms to take predefined actions the moment suspicious behavior is detected. These actions may include isolating a device from the network, terminating malicious processes, disabling compromised user accounts, or reverting system changes through rollback mechanisms. In advanced platforms, response logic adapts dynamically based on threat severity, minimizing disruption while stopping active attacks.
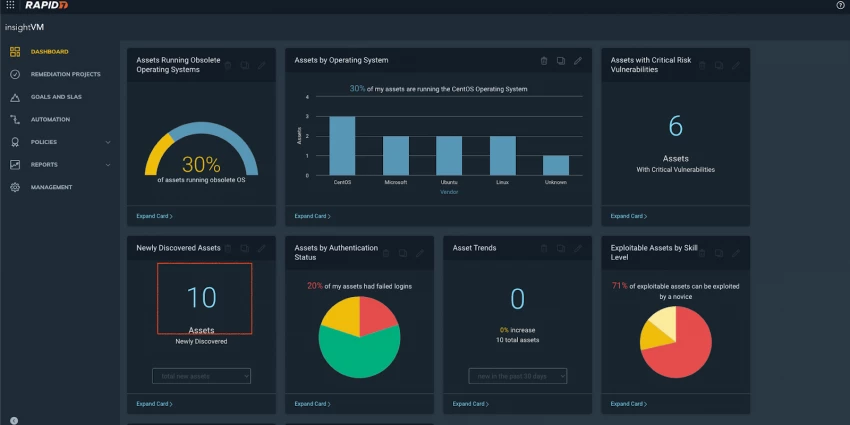
Vulnerability and exposure management shifts endpoint security from reactive defense to proactive risk reduction. Rather than waiting for exploits to occur, these tools continuously assess endpoints for missing patches, outdated software, insecure configurations, and known exploitable weaknesses. Many platforms prioritize vulnerabilities based on active exploitation in the wild, endpoint exposure, and business impact, helping IT and security teams focus remediation efforts where they matter most. This capability is especially important in environments where patching cycles lag behind attacker timelines.
Threat hunting and forensic analysis tools are designed for organizations that want to move beyond alerts and proactively search for hidden threats. These capabilities allow analysts to query endpoint telemetry across weeks or months of historical data, looking for subtle indicators of compromise that automated systems may miss. Advanced threat hunting supports hypothesis-driven investigation, such as searching for abnormal PowerShell usage, credential access patterns, or suspicious parent-child process relationships. When incidents occur, forensic tools provide detailed evidence to support containment, recovery, and compliance reporting.
At the high end of the market, Extended Detection and Response (XDR) platforms unify endpoint data with signals from identity systems, email gateways, cloud workloads, and network infrastructure. Instead of analyzing endpoint events in isolation, XDR correlates activity across domains to identify complex, multi-stage attacks. For example, a phishing email, followed by suspicious login behavior and endpoint privilege escalation, may appear low risk individually but become high confidence when correlated together. This broader context reduces false positives and improves detection of attacks designed to evade single-layer defenses.
Together, these features define what endpoint security means in 2026. The difference between platforms lies not in whether these capabilities exist, but in how deeply they are integrated, how effectively they automate response, and how usable they are for real-world security teams.
Endpoint security pricing in 2026 varies widely based on scale, features, and service level.
Small businesses typically pay $5 to $30 per endpoint per month, usually for cloud delivered protection with basic EDR capabilities.
Mid sized organizations often spend $40 to $100 per endpoint per year, depending on whether they add centralized management, advanced response, or MDR services.
Enterprise deployments frequently exceed $50 per endpoint per month, particularly when bundled with managed detection and response, long term data retention, and advanced analytics.
Key pricing factors include:
● Number of endpoints or users covered
● Feature tier, from basic AV to full XDR
● Deployment model, cloud versus on premises
● Add ons such as MDR, extended data retention, or compliance tooling
Annual contracts generally reduce costs, while per user pricing favors environments where employees use multiple devices.
Below is a closer look at major endpoint security platforms shaping the market in 2026, with a focus on features, strengths, and ideal buyers rather than just list pricing.
CrowdStrike remains one of the most widely deployed endpoint security platforms at the enterprise level. Falcon is cloud native, uses a lightweight agent, and is known for strong behavioral detection and threat intelligence.
Its modular pricing allows organizations to start with basic protection and layer on EDR, threat hunting, identity protection, and MDR. Falcon Complete, its managed service, is especially popular among companies without large SOC teams.
CrowdStrike is best suited for large organizations, cloud first environments, and security mature teams that value deep visibility and ecosystem integrations.
Microsoft Defender has matured into a serious competitor, particularly for organizations already invested in Microsoft 365 and Azure.
It offers solid EDR, automated investigation, and vulnerability management at a comparatively low price point. Tight integration with Windows, Entra ID, and Microsoft security tooling makes it attractive for SMBs and mid market firms.
While advanced threat hunting and cross domain visibility lag some competitors, Defender delivers strong value for cost conscious buyers operating within the Microsoft ecosystem.
SentinelOne differentiates itself through autonomous response and rollback capabilities. Its platform emphasizes minimal human intervention, using AI to stop and remediate attacks in real time.
The Singularity suite bundles NGAV, EDR, and optional XDR, with pricing tiers aligned to feature depth. It is especially popular with MSPs and lean security teams.
SentinelOne is well suited for organizations that prioritize automation and fast containment over deep manual investigation workflows.
Sophos positions Intercept X as part of a broader synchronized security ecosystem that connects endpoint, firewall, and MDR services.
Its strengths include ransomware protection, ease of use, and strong managed service offerings. Pricing is competitive for small to mid sized businesses, particularly those seeking an all in one security stack.
Sophos appeals to organizations that value operational simplicity and vendor consolidation.
Cortex XDR is built for large enterprises that want deep correlation across endpoint, network, and cloud data.
It excels in advanced analytics, UEBA, and large scale incident investigation, but comes with higher costs and greater complexity. Cortex XDR is often deployed alongside Palo Alto firewalls and security platforms.
This solution is best for security mature enterprises with dedicated SOC teams and complex environments.
Bitdefender offers a strong balance of affordability and advanced protection, making GravityZone popular with SMBs and managed service providers.
It provides solid exploit prevention, risk analytics, and cross platform coverage without the premium pricing of enterprise focused vendors.
GravityZone works well for smaller organizations that still want enterprise grade security features.
Several trends are influencing buying decisions this year.
AI driven detection and remediation is reducing alert fatigue and SOC workload.
XDR adoption continues as organizations seek unified visibility across endpoints, identity, and cloud workloads.
Managed Detection and Response is becoming a default add on rather than a premium service, especially for mid sized businesses.
Compliance and data protection features are gaining importance as regulations tighten around breach reporting and data handling.
Pricing models are also shifting toward bundled subscriptions that emphasize ROI metrics rather than raw feature counts.
There is no universal best endpoint security solution. The right choice depends on organization size, risk profile, and operational maturity.
Small businesses benefit from platforms that prioritize ease of deployment and cost efficiency. Mid sized organizations often seek a balance between automation and visibility. Enterprises require scalability, deep analytics, and integration with broader security ecosystems.
Before committing, buyers should evaluate:
● Visibility and response depth
● Integration with existing tools
● Total cost including services and training
● Vendor roadmap and support quality
Endpoint security in 2026 is no longer about stopping known malware. It is about detecting behavior, responding automatically, and maintaining visibility across an increasingly distributed workforce.
Pricing reflects that shift, with costs tied directly to intelligence, automation, and service depth. Organizations that treat endpoint protection as a strategic investment rather than a commodity are better positioned to manage risk, reduce downtime, and scale securely.
Choosing the right platform today is less about chasing features and more about aligning security capabilities with how your business actually operates.
Be the first to post comment!